Surat Urban Development Authority Accounts Assistant Using Tally Model Question Paper : sudaup.org
Organisation : Surat Urban Development Authority
Exam : ICT 701, 705 & 706
Document Type : Model Question Paper
Category or Subject : Accounts Assistant Using Tally
Website : http://sudaup.org/modelpaper.html
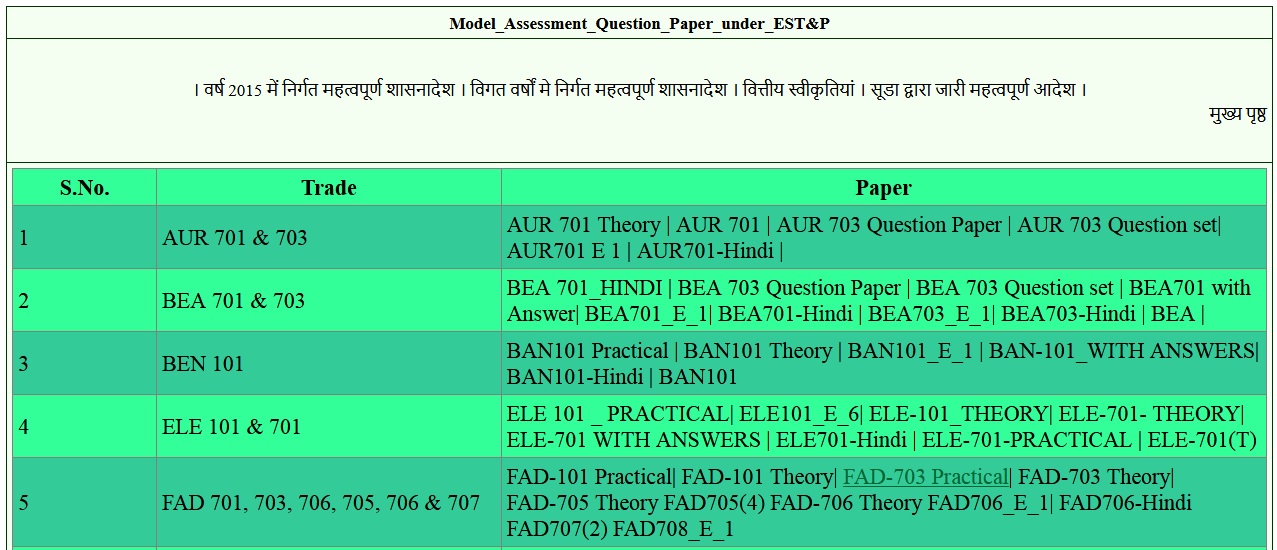
Download Model Question Paper :
ICT 701 Theory : https://www.pdfquestion.in/uploads/9621-ICT-701-Theo.pdf
ICT 701 Practical : https://www.pdfquestion.in/uploads/9621-ICT-701-Pra.pdf
ICT 705 Theory : https://www.pdfquestion.in/uploads/9621-ICT-705-PRA.pdf
ICT 705 Practical : https://www.pdfquestion.in/uploads/9621-ICT-705-THEO.pdf
ICT 705 VIVA : https://www.pdfquestion.in/uploads/9621-ICT-705-Viva.pdf
SUDAUP Accounts Tally Model Question Paper
Max. Time : 1 Hour
Paper : Theory Paper
Max. Marks: 50 Marks
Accounts Assistant Using Tally Model Question Paper :
Section-A :
Multiple Choice Questions (MCQ).
1. What is the full form of http?
a) HyperText Transmission Protocol
b) HyperText Transfer Protocol
c) HyperTerminal Transport Protocol
d) HyperTerminal Transfer Protocol
2. IRC stands for
a) Internet Related Chat
b) Internet Relay Chat
c) Internet Related Content
d) None of the above
3. What are the uses of the Internet?
a) Communication
b) Information Retrieval
c) Presentation of Information
d) All of the above
4. “ .net “ domain is used for
a) educational institution
b) Internet infrastructure and service providers
c) International organizations
d) None Of the above
5. SEO stands for
a) Search engine Operation
b) Search engine Optimization
c) None of these
d) Search entry Optimization
6. Full form of POP
a) Post Operational Protocol
b) Post Office Protocol
c) Preliminary Operational Protocol
d) None of these
7. The output quality of Printer is measured by
a) Dot per inch
b) Dot per sq. inch
c) dots printed per unit time
d) all the above
8. World wide web was proposed by
a) Bill Gates
b) ARPANET
c) Tim Berners-Lee
d) Bill Rogers
9. What are the uses of the Internet?
a) Communication
b) Information Retrieval
c) Presentation of Information
d) All of the above
10. ——————- command is used to print voucher
a) F3
b) Print
c) Print Voucher
d) none of these
11. The Function key to activate contra voucher is ———–
a) F3
b) F4
c) F2
d) F6
12. Cash book is ruled like —————-
a) Ledger Account
b) Saving account
c) Fixed account
d) None of these
13. Expense incurred on administration come under ————-expense group
a) Direct
b) Indirect
c) Default
d) None of these
14. Debit is in the ———– side of the account (Right)
a) Right
b) Left
c) End
d) None of these
15. Tally is a ———– software
a) ERP
b) Financial Database
c) Accounting
d) Recording
16.Comparing ratios of different months are called —————
a) Comparison Analysis
b) Ageing Analysis
c) Stock Ageing Analysis
d) Ratio Analysis
17.The irrecoverable debts are known as —————
a) Debts
b) Bad debts
c) Good Debts
d) Irrecoverable Debt
18. Sales Returns are entered in the —————– book
a) Inventory book
b) Account Book
c) Income Book
d) Sales Day Book
19. Loans and advances received are —————-
a) Assets
b) Income
c) Liabilities
d) None of these
20. Ctrl + V is used to delete a file
a) True
b) false
21. Alt + f10 is used for physical stock
a) True
b) False
22. Secured loans are in liabilities
a) True
b) False
23. E-Commerce stands for
a) Electric Commerce
b) Electrical Commerce
c) E-mail Commerce
d) None of these
24. Which of the following is not a type of cyber crime?
a) Hacking
b) Phishing
c) Cyber Stalking
d) Surfing Websites
25. Which of the following Is a Safe Browsing technique
a) Evaluating Your Web Browser’s Security Settings
b) Shopping Safely Online
c) Web Site Certificates
d) All of these
26. Which of the following is not a threat
a) Spyware
b) Shareware
c) Scareware
d) Adware
27. Full form of Virus is
a) Vital Information Resource under siege
b) Virtual Information Resource under store
c) Vital Information reserve under siege
d) Very Important Resource under siege
28. Which amongst the following is not an effective security measure?
a) User Authentication
b) Anti virus
c) Biometrics
d) Using USBs always
29. Which of the following is not an offense under IT Act
a) E-Mail Spoofing
b) Identity Theft
c) Spreading Virus and worms
d) Surfing
30. Which of the following is not an Internet Marketing Technique?
a) Search Engine Marketing
b) E-mail Marketing
c) Social Media Marketing
d) Texting